Digitalization now touches every area of our professional and personal lives. Be it communication, manufacturing, healthcare, or transport; without digital, modern operations would grind to a halt. As the applications of digital technology grow, however, so do their risks.
Every organization now has a responsibility to ensure that their operations are protected and secured against cyber security threats. From customer data to supply chains and machinery, digital defenses must be in place for every connected device and process. Businesses’ reputation and license to operate depends on their ability to protect themselves against cyber threats, but also on their ability to recover after an attack.
At Amaris Consulting, we believe that cyber security should be at the core of every organization; every department, every team member, and every business line should be aware of the risks and prepared to face them. We outline our take on cyber defense, incident response, training, and preparing for the threats of tomorrow so that your business can build resilience and protect itself, come what may.
The Stakes
Since 2013, over 3.8 million data records have been stolen every single day, and there is an attempted cyber-attack every 39 seconds. It is virtually inevitable that every business will experience an attempted hack at some point.
Successful attacks can have devastating consequences for businesses; as well as costing millions, – on average, share prices fall 7.27% after a cyber security breach – the reputational damage among customers, partners, and suppliers can be difficult to recover from. Furthermore, regulator’s penalties resulting from data breaches can significantly impact businesses; Europe’s GDPR includes fines up to the value of 4% of turnover.
Defense
The inevitability of an attempted attack means that having a proactive and efficient defense strategy in place is no longer optional. Far more than the simple firewalls and email filtering of days gone by, today’s cyber security measures should be far-reaching and as sophisticated as the hackers they are trying to deter and withstand.
A robust cyber defense reduces the appeal of your organization as a target, as an attack would necessarily be more expensive and time consuming for hackers but may also expose their activities. A good defense system should not only act as a deterrent, but also effectively detect and alert cyber security teams if an attack is in progress.
Cyber defense is a key area of expertise among Amaris’ Information Systems & Digital consultants, with penetration testing and security assessments forming the foundations of our strategic cyber security services.
We believe that when it comes to cyber security, prevention is always better than cure; a system of robust and resilient defenses using the latest techniques and technologies is the only way to maintain business continuity and adequately protect a company’s interests, as well as that of its clients and suppliers. We analyze current cyber trends using threat intelligence to protect against likely types of attack, as well as known hacking groups and common methods. This allows us to apply cutting-edge expertise and implement the latest defense technology to keep our clients protected and secure.
Training
Around 95% of cyber security breaches are caused by human error and disinformation. Ensuring that everyone in a company is fully aware of cyber security best practices and knows how to play their part in protecting the business is one of the most effective ways to maintain a secure environment. However, studies have shown that team members don’t always use best practice in their day-to-day working lives, even when they know they should.
Weak passwords are a commonly exploited means of hacking. 91% of respondents to a recent survey understood that reusing passwords is risky, and 59% know having a secure password is important. Despite this, more than half (61%) reused passwords and 41% used a password they knew to be weak.
At Amaris, we understand that behavioral science plays a key role in changing behaviors to protect businesses. Getting team members on board with the reasons why cyber security is so important is far more effective than attempting punitive measures after the fact; people respond more positively to the carrot than the stick.
One third of people confess to rarely or never thinking about cyber security when they’re at work. For teams to take affirmative action in embedding cyber security into their daily work, motivation, ability, and a prompt must all be in place.
Blank
Motivation can come in the form of incentives or social proof – no one wants to be responsible for letting the rest of their team down, so highlighting teams with the best security performance or congratulating teams for exemplary processes can be effective encouragements. Ability comes in the form of technical knowledge, understanding exactly why cyber security is important, the risks posed by poor security, and the outcome of any breaches. Prompts can be manager emails, periodic security checkups, or even monthly calendar reminders to change passwords or install updates.
We provide extensive cyber security training services for our clients all over the globe. Amaris’ consultants can identify key knowledge gaps and training needs, offer support and training on IT systems, and facilitate workshops for team members on cyber security and its importance in a company setting.
It is our belief that cyber security concerns every employee of a business, and our tailored training ensures that this knowledge and expertise is accessible, relatable, and relevant, whatever department or business area teams may come from.
Incident Response
Despite the very real and pressing threat of cyber breaches, more than one in ten (14%) organizations do not have a cyber security emergency response plan in place. Just as worryingly, a further 12% of respondents to a recent survey didn’t know if they had such a plan. 20% of business leaders don’t know what to do during a breach.
In today’s hyperconnected world, a major problem facing organizations is that they are just as vulnerable to attacks on their partners and suppliers as they are to direct attacks on their own systems: malware, worms, or viruses can spread extremely efficiently through linked systems, emails, platform interfaces, and other connections. The result is that even if your business is secure, you may still be more vulnerable than you think, hence the need for an efficient and rapid response plan to any type of cyber incident.
At Amaris, we believe in a 3-step approach to cyber incident response: preparation, identification & containment, and recovery.
Preparation: As with any developing event requiring a quick response, the people who are most equipped to deal with a situation are the ones who have received training. Planning for each stage of a cyber-attack and ensuring that each team member knows what to do can be the difference between a breach and a near miss.
Having procedures and policies in place to ensure that best practice guidelines are followed, all team members are aware of how to protect themselves and the company, and that IT system and devices conform to the latest security standards are all crucial steps in preparing for an attack.
Identification & containment: Cyber-attacks can spread rapidly throughout a company’s IT infrastructure so it’s important to shut down an attack as rapidly as possible. This mitigates the effects of any cyber-attack that does manage to penetrate a company’s defenses.
Being aware of any attacks in progress goes hand in hand with containing the threat identified. Stopping an attack can involve taking systems offline, restoring ‘clean’ backups, and quarantining devices or networks. Having the right professionals in place to correctly identify threats, raise the alarm with the right stakeholders, and take appropriate action to contain the threat is critical in building business resilience to cyber threats.
Recovery: Once a threat has been neutralized, recovery can begin. This can include systems recovery by restoring data or software from secure backups, but it also refers to a business’ return to normality after a cyber incident. After ensuring that the attack has ceased and that the vulnerabilities which allowed the cyber-attack are secured to prevent a repeat incident, systems can gradually be brought back online and operations resumed with close monitoring.
Taking stock of what data may have been compromised or stolen should be a company’s next step; ensuring that financial and proprietary data remains secure will be a priority for most. This will facilitate cost calculations and establish the damage caused. Most data protection laws also require businesses to notify regulators within 72hrs of a breach, so accurately assessing an attack’s scope and scale must be done quickly.
The recovery stage ends with implementing learnings gained from the incident. Defending any weaknesses in security, installing the latest IT security updates, and providing further training can all be necessary depending on the nature of the attack. An evaluation and report should always be completed post-incident to determine how future improvements can be made.
Taking a holistic approach to incident response ensures that businesses reduce their risk and can lessen the effects of any cyber defense penetration. Amaris’ consultants are on the front line of cyber incident response, giving them cutting-edge insight and experience in managing even the most sophisticated cyber-attacks. We believe that cyber-attacks will continue to evolve and grow more frequent, and that incident response will have to be deeply embedded into not just IT professionals’ processes, but company wide.
The threats of tomorrow
Cyber security must keep pace with cyber threats, which are constantly evolving. As well as defending against current known threats, at Amaris we are also continually assessing the vulnerabilities of tomorrow.
The new technologies and extensive digitalization we have seen over the past decade show no sign of slowing down. Businesses will therefore continue to become ever-more vulnerable to cyber-attacks as the number of connections increases. Just some of these threats of tomorrow are addressed below, but organizations should ensure that they fully understand the risks associated with any digitalization or technology they bring into their environments.
AI: Today’s world is already saturated with AI: biometric IDs, translation software, driverless vehicles, satellite navigation, and personal assistants are all AI-enabled technologies with the potential to be hacked. As the accessibility, applications, and capabilities of AI grow, so do the risks.
The World Economic Forum warns that one of the most likely form of AI-enabled attacks will be ‘supercharged’ phishing. Since the phishing attacks of today are performed at scale they tend to be generic and easily identifiable by individuals; AI’s ability to replicate language style and adapt to context means these attacks can now be highly tailored, credible, and sophisticated, making them much harder to spot and defend against.
Blockchain hacking & cryptojacking: Blockchains have become popular in many industries due to their supposed incorruptibility and the permanence of their records, and they are becoming a mainstay in finance.
Blank bbbbbbbbb
These security features are a double-edged sword, however, as the fundamental benefits of a blockchain also mean that fraudulent transactions cannot be reversed. Since 2017, hackers have stolen over $2 billion worth of cryptocurrency. As well as hacking crypto platforms, cyber criminals are also hijacking devices’ processing power to mine bitcoins without users’ knowledge. The software used is easy to deploy and hard to detect, and it can infect devices through malware, hacked infrastructure, or even cloud systems. Slower computer response times, increased processor usage, overheating computer devices, and higher electricity bills are the inevitable consequences of cryptojacking.
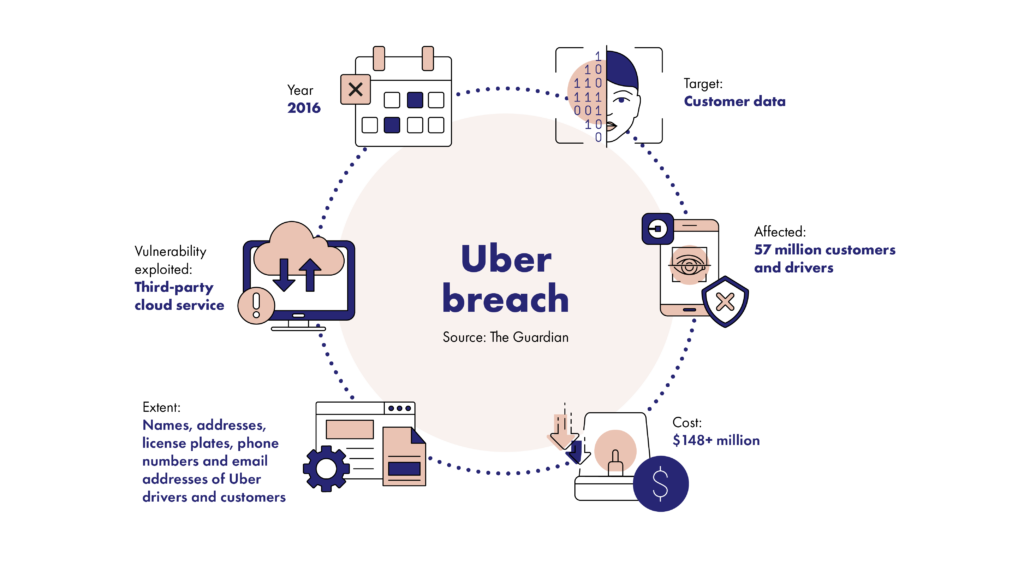
Cloud systems: Organizations have been gradually moving away from proprietary data servers and onto cloud environments for many years. From software-as-a-service (SaaS) such as Microsoft Office 365 to infrastructure-as-a-service (IaaS) like Amazon Web Services (AWS), most businesses are now exposed to multiple cloud platforms. Attacks on cloud environments correspond to this trend; they more than doubled in 2019 and now account for around 20% of all cyber incidents.
Most cloud system suppliers offer their service with a shared security responsibility; the customer is responsible for securing data and access, while the supplier secures the system itself. The problem is that when a malicious actor has gained access to a cloud system, they are able to inflict extensive damage to data, steal swathes of information, and destroy crucial operating information. It’s therefore up to businesses themselves to ensure that whatever is on the cloud remains secure.
Ensuring that IT infrastructure and security policies and practices are watertight, and that regular maintenance, updates, and security patches are in place will help businesses to maintain continuity; it will also enable them to recover quickly from any successful attacks. Deploying multi-level security and having the right experts in place to plan, prepare, manage, and recover from cyber incidents are now intrinsic to business resilience.
At Amaris, we pride ourselves on having the right people on hand to help our clients around the world across a variety of industries and sectors. Cyber security is no longer the domain of IT professionals only; every person within an organization has the power to prevent an attack, and to raise the alarm if one is identified. As attacks can come from any direction at any time, maintaining preparedness and ensuring that cyber security is front-of-mind across a company is key.
For more information on Amaris’ cyber security competencies and our Information Systems & Digital capabilities, visit www.amaris.com